Phone Spoofing Explained: What It Is and How to Protect Yourself

- What is phone spoofing?
- How does phone spoofing work?
- Spoofing 101: Different Ways Cyber Attackers Disguise Themselves
- The Dangers of Phone Spoofing in Online Banking and Financial Transactions
- Real-life scenarios of phone spoofing
- How to protect yourself from phone spoofing
- Stay vigilant of phone spoofing
- Faq
“The call looks real. The voice sounds familiar. But the person on the other end isn’t who you think.”
In today’s connected world, cybercriminals can easily impersonate individuals, including bank managers or family members. With personal data stored online, tracing these threats has become increasingly complex. By 2025, scammers are expected to have advanced to using AI-powered voice cloning and deepfake technology, making fraudulent calls increasingly challenging to detect.
Infosprint Technologies, a cybersecurity solutions provider, recognizes the threat posed by caller ID spoofing and has researched effective ways to protect yourself from these evolving attacks.. This blog examines the phenomenon of phone spoofing, its rise, and how to safeguard your data and maintain trust.
What Is Phone Spoofing?
Phone spoofing is a technique used by fraudsters to communicate with others by falsifying their caller ID information. Instead of displaying the caller’s real phone number, the spoofed number may appear as that of a reputable organization — such as a bank, government agency, or even someone you know, like a friend or relative.
The scammer’s objective is to fool you into taking the call and trusting the source, which can lead to the unintentional disclosure of personal data or the authorization of transactions.
How Does Phone Spoofing Work?
Cybercriminals disguise themselves to gain your trust by impersonating a legitimate source. Caller ID spoofing works by tampering with the technology that transmits caller ID data between phone networks. Scammers commonly use Voice over Internet Protocol (VoIP) services or specialized software to alter the number that appears on your phone’s caller ID.
In 2025, some attackers have taken this further, using AI voice synthesis to replicate the voices of real people, such as bank representatives or law enforcement officers. This makes spoofing attacks more convincing and dangerous, particularly in regions such as Canada and Singapore, where the banking and telecom sectors are heavily digitalized.
For instance, scammers may impersonate police officers and claim that you have committed fraud by simply stating your name and mobile number. This strategy compromises your judgment and pressures you to provide personal information, such as your address, email, Aadhaar number, or family details. Once they have this data, they may instruct you to install malicious apps that secretly access your device and financial data.
Spoofing 101: Different Ways Cyber Attackers Disguise Themselves
According to recent cybersecurity reports, over 60% of mobile users receive at least three spam or spoofed calls daily. Recognizing the type of spoofing attempt is crucial to staying safe.
Here are some of the ways scammers use caller ID spoofing:
- Neighbor Spoofing: Scammers use the same area code as their victims to create a sense of familiarity, increasing the chances that the call will be answered.
- Government Agency Spoofing: This technique aims to intimidate victims into providing personal details or making payments under the guise of law enforcement or tax agencies.
- Bank Spoofing: When a fraudster’s call appears as if it’s coming from your bank’s official number, urging you to share OTPs or verification details to “secure” your account.
- Customer Care Spoofing: Cybercriminals impersonate the support lines of trusted brands to collect account credentials and personal information.
- Voicemail Spoofing: Attackers leave pre-recorded voice messages urging victims to call back about an “urgent matter,” leading them into a scam.
- AI Voice Spoofing (New Trend): In 2025, scammers began using AI voice cloning to replicate real voices. The Canadian Anti-Fraud Centre (CAFC) reports a surge in cases where fraudsters mimicked bank representatives or family members to request verification codes or transfers.
For a deeper dive into how social-engineering tactics accelerate during major shopping seasons, see our post on “5 Ways Social Engineering Gets More Sophisticated During Holiday Sales — and How to Defend
The Dangers of Phone Spoofing in Online Banking and Financial Transactions
Phone spoofing poses a significant risk to online banking and financial transactions. With digital payments becoming the global norm, spoofing has evolved into one of the most effective tools for cybercriminals.
1. Fraudulent Account Access
Scammers impersonate bank staff, requesting OTPs or PINs under the pretext of verifying suspicious activity. Once obtained, they gain unauthorized access to accounts and conduct illicit transfers within seconds.
In early 2025, a Toronto resident fell victim to such a scam, losing over $200,000 after receiving calls from individuals impersonating RCMP officers and her bank’s fraud department. Despite showing legitimate caller IDs, the calls were spoofed through VoIP masking.
2. Identity Theft
Using caller ID spoofing, criminals collect personal data — names, dates of birth, banking details — to open fraudulent credit lines or apply for loans under stolen identities.
3. Phishing and Vishing Attacks
Phone spoofing amplifies traditional phishing. “Vishing” (voice phishing) occurs when scammers call pretending to be from trusted institutions. Victims are lured into visiting fake banking sites or disclosing sensitive credentials.
4. Social Engineering Scams
Spoofing supports larger social engineering attacks, where scammers impersonate advisors, managers, or law enforcement. Victims are manipulated into wiring money, investing in fake opportunities, or providing confidential security details.
5. Business Compromise
Corporate phone spoofing remains a global issue. Criminals spoof executives’ numbers to trick employees into transferring funds. These Business Communication Compromise (BCC) incidents mirror email-based BEC scams and are particularly prevalent across North America and Asia.
To explore broader online-banking data-security practices, you may also refer to our article Protect Your Finances: 5 Most Effective Online Banking Data Security Practices to Implement Now”
Real-Life Scenarios of Phone Spoofing
Recent incidents highlight the global scale of this threat:
- In Canada, multiple reports from 2024–25 indicate that spoofed RCMP and Service Canada calls have led to significant financial losses.
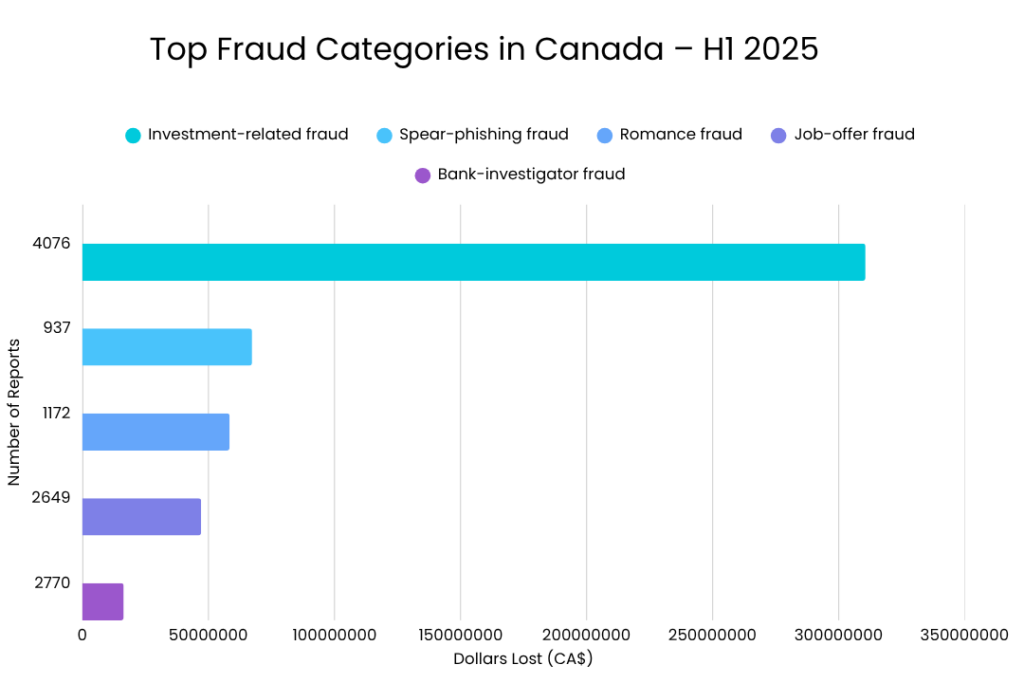
- In the U.S., scammers mimicked Chase Bank and Zelle representatives to steal one-time passcodes from users.
- In Singapore, AI voice spoofing was used to imitate bank agents from DBS in a coordinated phishing campaign.
These examples demonstrate that, despite regional differences, cybercriminals employ universal tactics — exploiting trust, urgency, and new technology.
How to Protect Yourself from Phone Spoofing
Knowing how to defend yourself is essential to avoid becoming a victim. Below are practical ways to secure personal and financial data from caller ID spoofing scams:
- Be Wary of Unsolicited Calls:
Even if the caller ID displays a trusted name, verify the identity before sharing any information. Hang up and call back using the organization’s official number. - Never Share Sensitive Data:
Account numbers, passwords, and OTPs should only be given if you initiated the call and confirmed the source. Legitimate banks will never request these details over the phone. - Enable Multi-Factor Authentication (MFA):
Even if your credentials are stolen, MFA prevents unauthorized access. - Use Verified Calling Features:
In Canada and the U.S., carriers now use STIR/SHAKEN technology to verify caller authenticity. Look for “Verified Call” indicators on smartphones. - Use Call-Blocking Apps and Services:
Several providers globally (Bell, Verizon, Singtel, Airtel) offer AI-powered call filters that identify suspected spoofed calls. - Report Suspicious Activity:
- Canada: Report to the Canadian Anti-Fraud Centre (CAFC) or CRTC Spam Reporting Centre.
- U.S.: Report to the FTC’s Do Not Call Registry.
- Asia-Pacific: Utilize local cybersecurity helplines or support from your telecom provider.
- Canada: Report to the Canadian Anti-Fraud Centre (CAFC) or CRTC Spam Reporting Centre.
- Monitor Accounts Regularly:
Set alerts for large withdrawals or unusual login activity to detect fraud early.
For a deeper dive into mobile device security best practices, especially now that phone spoofing often begins with a mobile app or SMS link, see our companion article, Mobile Security 101: Protecting Your Phone from Modern Cyber Threats.
Stay Vigilant Against Phone Spoofing
In our increasingly interconnected world, phone spoofing continues to evolve, with the use of AI and cross-border fraud networks making scams more convincing than ever. Whether it’s a deepfake voice or a spoofed police call, awareness and caution remain your best defenses.
By understanding how spoofing works and adopting preventive measures, such as multi-factor authentication, verified calling, and prompt reporting, you can protect both personal and professional data.
As spoofing threats expand globally, from Toronto to Singapore, Infosprint Technologies remains committed to helping individuals and enterprises build resilient, secure communication environments. Connect with our cybersecurity experts to strengthen your organization’s protection against the next wave of digital threats.
Frequently Asked Questions
If the caller ID looks official but asks for OTPs, passwords, or urgent action — it’s likely spoofed. Hang up and verify by calling the official number directly.
Yes. Scammers use VoIP and number-masking tools to display real institutions’ numbers, making their calls appear completely legitimate.
Immediately contact your bank, change your passwords, enable MFA, and report the incident to your country’s fraud reporting authority (like CAFC or FTC).
Modern spoofing uses AI and global VoIP routes, hiding the caller’s true origin. Deepfake voices make detection even more difficult in 2025.
Enable multi-factor authentication, use call-blocking apps, and look for “Verified Call” indicators. Always stay skeptical of unsolicited calls — even if they look familiar.
Related Posts
Top 10 Cloud Computing Technologies to Look Out for in 2025

Consistent Diagnosis: The Cornerstone of Modern Healthcare




