Festive Sale Scams 2025: How Fake Shopping Sites Steal Your Payment Data
Nearly 69% consumers make impulsive purchases during festivals, often skipping even basic security checks.
The jingling bells and “limited-time” deals lower our guard — and that’s exactly when cybercriminals strike. With that lowered vigilance, cybercriminals craft fake feast-time deals that look dazzling on the surface — but silently harvesting your payment data.
At Infosprint Technologies, we believe digital celebrations shouldn’t compromise online security. In this blog, see how fake stores and checkout scams steal your data, the key red flags and steps to take for companies and customers to safeguard their data.
Rise of Fake Discount Campaigns & Spoofed E-Commerce Sites
1.1 Festive Discount Mania: A Perfect Storm
Festivals are retail goldmines. Brands slash prices, marketers blast promos, and shoppers sprint to catch deals. Fraudsters exploit this climate — knowing that people are primed to click. They launch time-limited “flash sales,” “secret codes,” and “exclusive festive coupons” that bypass your guard by promising huge savings.
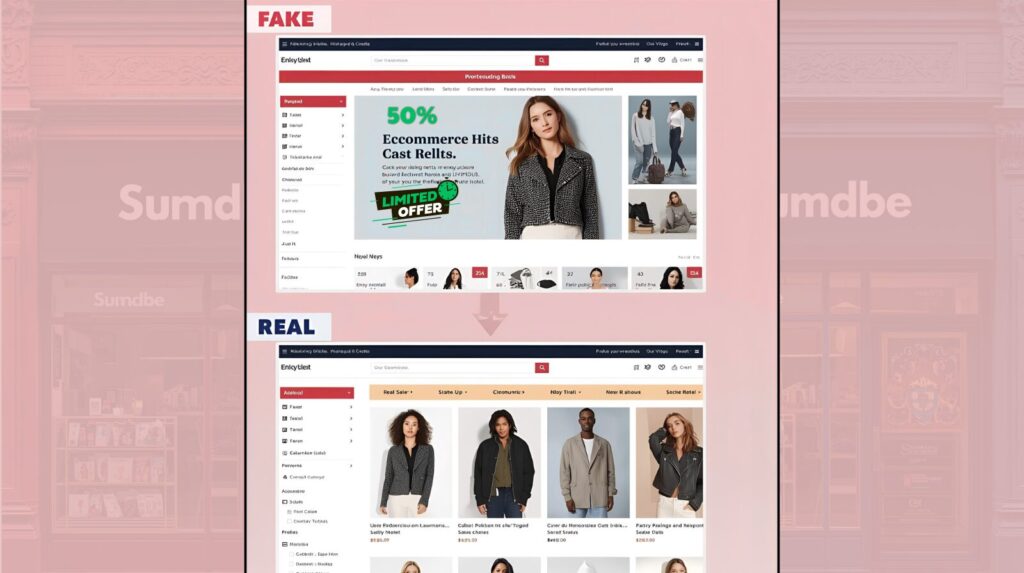
1.2 The Anatomy of a spoofed site
- Copy the look:
Fraudsters often mirror logos, product images, and layouts to make the site appear authentic. - Use deceptive domains/subdomains:
Look-alike domains (tiny typos) or brand-as-subdomain hide the real URL. - Seed via messages & ads:
SMS, WhatsApp, and targeted social ads drive traffic during festival hype. - Create artificial urgency:
Flash sales, countdowns, and “limited stock” prompts push users to act fast. - Harvest at checkout & hide it:
The “Buy Now” button leads to fake payment forms that capture card data, then display processing/failure screens to cover their tracks.
1.3 Why Is This Booming Now?
- Low barriers to setup: With off-the-shelf storefront builders, APIs, and phishing kits, fake stores can go live in minutes.
- High payoff: A few successful payments — even small ones — can net hundreds or thousands in stolen data.
- Difficult to police: Domains change, servers shift globally, and legal recourse is slow.
- Blind trust during celebration: Users often trust deals more during festivals, believing “everyone’s buying this” or “this is official.”
How Cybercriminals Steal Your Payment Data
2.1 Fake Checkout Pages as Data Traps
The checkout is the attacker’s endgame: here’s the step-by-step funnel that turns your card details into stolen data.
- Add-to-cart lure: Victim completes shopping on a spoofed storefront and clicks the checkout CTA.
- Fake form served: The checkout page hosts a form that looks legitimate but posts data to attacker-controlled endpoints.
- Mirror verification UI: Attackers display familiar bank/gateway fields (e.g., OTP, CVV) directly on the fake page to avoid suspicion.
- Masking delay: “Processing…” / “Redirecting…” screens keep the user waiting while data is exfiltrated.
- Cover tracks: Show “payment failed” or disappear — the user believes a glitch, while the attacker keeps the captured data.
2.2 API Hijacks & Man-in-the-middle (MITM) Attacks
These are backend-level interceptions where the fraud happens between your site and the payment provider.
- Target integration: Attackers identify vulnerabilities in payment gateway integrations, plugins, or third-party scripts that can be exploited to compromise sensitive data.
- Inject malicious code: Compromised JS or a rogue plugin is added to the checkout flow.
- Intercept traffic: The injected code captures card payloads as they move to the gateway (or tampers with the API call).
- Duplicate to hidden endpoints: Transaction data is silently duplicated and forwarded to attacker servers.
- Transaction appears normal: The legitimate payment still processes, making detection difficult for both users and merchants.
For more information on securing APIs, refer to our Cloud Security in 2025 blog.
2.3 Malware, Browser Plugins, and Session Hijacking
Client-side compromises—such as malware or malicious extensions—can alter checkout behavior and steal sessions or form data.
- Distribution vector: Users are tricked into installing “deal-finder” extensions or malware from fake promos.
- Form/action modification: The extension or malware rewrites the form’s action or intercepts form submissions.
- Cookie & session capture: Session tokens or cookies are stolen, allowing attackers to replay or hijack checkout sessions.
- Silent exfiltration: Data is sent to attacker domains while the user experiences a normal checkout.
- Blend with other attacks: Often combined with phishing or backend compromises to maximize data haul and resilience.
Learn how to protect AI-built apps in our Low-Code App Security guide
Red Flags Every Shopper Should Notice

3.1 Too good to be true — the grand red flag
If an offer seems absurd — 90% off on big brands, brand new iPhones for ₹1,000, or “sitewide 95% flash sale” — it’s likely bait. Genuine retailers rarely discount that steeply, especially on flagship items.
3.2 Inspect the URL and domain
Look for small misspellings, extra words or hyphens, subdomain tricks, or domain mismatches (e.g. “festivedeals-shop.com/amazon”). Also check for HTTPS and a valid certificate (padlock icon) — though even that can be faked or easily acquired for a fake domain.
3.3 Check payment page behavior
- Does the checkout page open in a new tab or window?
- Does the URL change or redirect strangely when entering payment info?
- Is there any delay or odd “processing” screen?
- Do you see card logos, but clicking them doesn’t shift you to a recognized banking or gateway domain?
3.4 Ask for too many permissions
Ethical retailers don’t need you to install browser extensions, mobile apps, or give them extensive permissions just to place an order. Avoid clicking “Install this deal-assistant” or

Save Weeks of Analysis
3.5 Grammatical or UI inconsistencies
The presence of poor grammar, spelling errors, awkward layouts, mismatched fonts, or inconsistent branding can be telltale signs of a hastily built fraudulent site.
What Consumers Can Do
4.1 Verify the seller
- Search reviews, ratings, and complaint forums.
- Look at the domain registration date — if the site was just created days ago, be wary.
- Use official apps or websites (type the domain manually rather than following unknown links).
4.2 Always enable two-factor authentication (2FA)
Even if your card data is compromised, Two-factor authentication (2FA) is an extra security measure. Use OTPs, authenticator apps, or hardware tokens wherever possible — especially for your banking or wallet apps.
4.3 Use trusted networks & avoid public Wi-Fi
Public Wi-Fi is a playground for hackers. Always use your mobile data or a VPN (virtual private network) when making payments. This prevents man-in-the-middle interception on open networks.
4.4 Use virtual or disposable cards
Some banks or fintech services let you generate one-time or virtual card numbers with limited usage/expiry. Even if stolen, the damage is limited.
4.5 Confirm the payment URL before entering data
Verify that the payment form redirects to your bank or a well-established gateway domain, using a valid SSL certificate and a padlock. Don’t submit if anything seems off.
4.6 Keep software & devices updated
Ensure your browser, OS, and security software are current — patches often close vulnerabilities exploited by malicious scripts or extensions.
4.7 Monitor statements & set alerts
Check your bank statements frequently for any unusual activity, and let SMS/email alerts for payment activity, and have immediate recourse (contact bank) in case of unexpected charges.
How E-commerce Businesses can Secure Payment Gateways & APIs
5.1 Use trusted, PCI DSS–compliant gateways
Partner with payment service providers (PSPs) that are certified for PCI DSS (Payment Card Industry Data Security Standard). These gateways abstract away much of the complexity of securely handling card data.
A leading supermarket chain in South India partnered with Infosprint Technologies and underwent a comprehensive PCI DSS audit to fortify its payment systems against such threats.
5.2 Tokenization & vaulted cards
Never store full card details on your servers. Use tokenization — storing only a reference token in your DB. The actual card data is handled and stored securely by the gateway. This way, even if your database is compromised, payment data remains safe.
5.3 Input sanitization & CSP (Content Security Policy)
Sanitize all inputs, remove or audit third-party scripts, and enforce strict Content Security Policies so that unauthorized scripts can’t inject malicious code.
5.4 Use strong authentication and secure integration
- Use mutual TLS or certificate pinning between your server and payment gateway.
- Whitelist IPs for API endpoints.
- Enable HMAC signatures or request signing to verify payload integrity.
- Validate all callbacks/webhooks (e.g., use a secret token so that only your systems can trigger them).
5.5 Regular audits, penetration testing & code review
Hire security experts or bug bounty testers to probe your checkout flow, API endpoints, plugin ecosystem, and server infrastructure. Simulate MITM, plugin compromise, DNS spoofing, or API interception attacks.
5.6 Monitor anomalies and logging
Track payment anomalies, sudden spikes in failed payment attempts, repeated invalid card entries, or unusual geographies. Maintain comprehensive logging (including access logs, transaction logs, and API logs) and set up alerting mechanisms. If something seems off, temporarily stop checkout flows until it is validated.
5.7 Educate your user base
Display security badges, educate users about phishing risks, and communicate via verified channels during festivals (don’t send payment links via random SMS). Encourage users to verify domain names or reach out to your support if they get suspicious links.
Get FREE Checkout System Audit
Stay Festive, Stay Vigilant
In the glow of festival lights, the last thing you want is for your celebrations to be hijacked by a fake festive online shopping discount deal. Scammers exploit the very enthusiasm you feel during the season — but awareness and preparation can outsmart them.
Want peace of mind that your payment systems are breach-ready?
Get a free security check today — our team will audit your checkout flow, APIs, and integrations to ensure your systems stay safe before the next big sale rush.
Contact Us to Schedule Your Free Security Check
Frequently Asked Questions
Check the URL for typos or subdomain tricks, look for recent domain registration, verify contact info and reviews, and be suspicious of unrealistic discounts. Tools like ScamAdviser / government guidance also help.
No — HTTPS only indicates a TLS connection. Fake sites can still have TLS. Also verify the domain, certificate owner, and where the payment form submits data.
Attackers inject malicious JS or compromise plugins to intercept traffic between the site and payment gateway, duplicating or siphoning payloads to hidden endpoints. Detection needs code audits and signed API calls
Yes — virtual or single-use card numbers limit the damage if card details are stolen and are recommended for uncertain merchants.
Disable the checkout flow, rotate API keys/certificates, audit recent plugin/script changes, check server logs for unusual POST destinations, and notify customers + payment provider. Conduct a full security audit
Related blogs
Top 10 Cloud Computing Technologies to Look Out for in 2025

Consistent Diagnosis: The Cornerstone of Modern Healthcare




