API VAPT Explained: How to Secure Endpoints & Stop Data Leaks

- Why API Security Matters More Than Ever
- How API VAPT Works
- Types of APIs That Need VAPT
- Benefits of API VAPT
- Common Tools and Frameworks for API VAPT
- 7 Best Practices for API VAPT and Endpoint Protection
- Real-World Case Study: The Cost of Ignoring API Security
- How Infosprint Technologies Secures APIs with VAPT
- Checklist: API VAPT Test Cases That Catch Real Flaws
- Don’t Let APIs Be Your Weakest Link
- FAQs
90% of web-enabled applications expose more attack surface through APIs than the user interface itself.
APIs form the foundation of current digital ecosystems, powering everything from mobile apps and cloud integrations to payment gateways and IoT devices. But with this power comes risk.
This is where API Vulnerability Assessment and Penetration Testing (API VAPT) comes into play — not as a one-time exercise but as an ongoing security strategy that protects sensitive data, ensures compliance, and builds customer trust.
In this guide, we’ll unpack everything you need to know about API VAPT — from what it is, why it matters, and how it works, to best practices and real-world prevention strategies.
What Is API VAPT?
API VAPT is a dual-layered security process that identifies, analyzes, and exploits potential weaknesses in your APIs — before attackers can.
- Vulnerability Assessment (VA): Focuses on discovering known vulnerabilities using automated tools and scanners.
- Penetration Testing (PT): Simulates real-world cyberattacks to evaluate how those vulnerabilities can be exploited and the potential impact on your systems.
Together, they form a proactive defense mechanism that goes beyond basic API monitoring — revealing both technical flaws and logical security gaps.
Why API Security Matters More Than Ever
APIs are designed for connectivity — but every endpoint you expose is a potential doorway for attackers.
Some eye-opening statistics:
- 41% of organizations experienced an API-related data breach in the past year (Salt Security, 2024).
- 83% of exposed APIs lack proper authentication or authorization mechanisms.
- One in four data leaks in cloud-based environments originates from insecure APIs.
Common API Threat Scenarios
- Broken Authentication: Attackers gain unauthorized access by exploiting weak API tokens or credentials.
- Excessive Data Exposure: APIs return more data than necessary, leaking sensitive information.
- Injection Attacks: SQL, XML, or command injections manipulate requests to access backend databases.
- Rate Limiting Issues: Lack of throttling enables brute-force or denial-of-service attacks.
- Business Logic Flaws: Exploiting workflow loopholes in APIs to manipulate transactions or access restricted data.
APIs aren’t just software connections — they’re the new security perimeter. And without structured testing, your endpoints can quickly become your weakest link.
For example, in our review of the 5 Most Alarming Healthcare Data Breaches, many APIs were the root cause of the leak.
How API VAPT Works
The VAPT process follows a structured methodology to ensure no stone is left unturned. Here’s how professionals typically approach it:
Step 1: Scoping and Mapping
Identify the APIs in use — both public and internal. This includes REST, SOAP, GraphQL, or WebSocket-based APIs.
Then, define the scope:
- Which endpoints are in the testing scope?
- What authentication methods are used?
- What data flows and third-party integrations are in place?
Step 2: Vulnerability Assessment
Using automated tools (like Burp Suite, OWASP ZAP, or Nessus), security testers scan for:
- Input validation flaws
- Broken authentication
- Missing encryption
- Weak rate-limiting
- Insecure error handling
This phase provides a vulnerability inventory — a list of issues ranked by severity.
Step 3: Penetration Testing
Here, ethical hackers go deeper — manually exploiting the identified vulnerabilities to simulate real-world attack scenarios.
For example:
- Attempting privilege escalation using API tokens
- Manipulating request payloads
- Fuzzing endpoints to identify data leaks
- Intercepting API calls via proxy tools to test encryption
Step 4: Reporting
A detailed report is created showing:
- The vulnerability details
- Exploitation method
- Potential impact
- Risk rating (critical, high, medium, low)
- Recommended remediation steps
Step 5: Retesting & Verification
Once developers have fixed the issues, a retest is conducted to confirm that all vulnerabilities have been effectively resolved.
Types of APIs That Need VAPT
Not all APIs are created equal, but every API handling sensitive or business-critical data requires VAPT.
Here are the major categories:
- Public APIs: Open for external developers or customers (e.g., fintech APIs).
- Internal APIs: Used within company systems — often overlooked but equally vulnerable.
- Partner APIs: Enable third-party integrations and data exchange.
- Composite APIs: Combine multiple service calls — if one part is weak, the entire chain is exposed.
If your API handles personal data, payment information, or business logic, it’s a candidate for VAPT.
Don’t forget that partner or vendor APIs are often overlooked — for a deeper look at vendor-risk management processes, see our Startup Guide to Vendor Risk Management.
Benefits of API VAPT
Beyond compliance, API VAPT delivers tangible value across your business and technology ecosystem.
1. Prevents Data Leaks
By simulating real attacks, VAPT identifies insecure endpoints before malicious actors do — preventing data exposure, credential theft, or customer information leakage.
2. Strengthens Authentication & Authorization
Testing ensures the proper implementation of OAuth, JWT, and API keys, thereby reducing risks associated with token reuse or privilege escalation.
3. Ensures Regulatory Compliance
Compliance frameworks such as GDPR, HIPAA, PCI DSS, and ISO 27001 require secure data handling, which includes the use of APIs. VAPT helps you demonstrate adherence during audits.
4. Builds Customer Trust
Customers trust brands that prioritize data security. A VAPT-certified API environment signals maturity, transparency, and credibility.
5. Improves DevSecOps Integration
Integrating VAPT results into CI/CD pipelines promotes continuous security validation, fostering a shift-left approach in API development.
Common Tools and Frameworks for API VAPT
Professional testers leverage a combination of open-source and commercial tools for deeper insights:
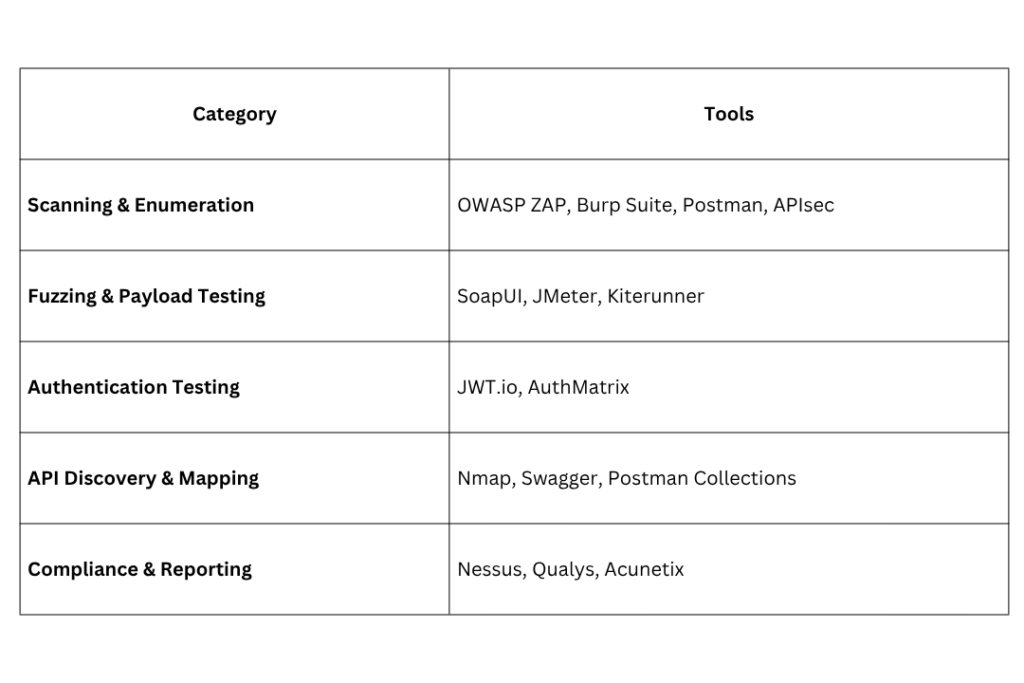
Additionally, security standards such as the OWASP API Security Top 10 and NIST SP 800-115 guide best practices for systematic testing and documentation.
7 Best Practices for API VAPT and Endpoint Protection
1. Maintain a Complete API Inventory
Untracked APIs — often referred to as shadow APIs — are one of the most significant risks to consider. Maintain an updated inventory of all internal, external, and partner APIs.
2. Use Strong Authentication & Authorization
Consistently implement token-based authentication (OAuth 2.0, JWT) and fine-grained role-based access controls (RBAC).
3. Validate Input Strictly
Reject unexpected parameters, sanitize inputs, and validate data types to prevent injection attacks.
4. Enforce Rate Limiting and Throttling
Limit API requests per user or IP to prevent brute-force and DDoS attacks.
5. Data Security Across Transmission and Storage
Use TLS 1.3 or above for transmission and encrypt sensitive fields in your databases.
6. Implement Continuous Monitoring
Use API gateways, WAFs (Web Application Firewalls), and security analytics tools to detect unusual traffic patterns.
7. Regularly Conduct VAPT
Schedule periodic testing — especially after API updates, integrations, or new deployments — to ensure optimal performance.
Real-World Case Study: The Cost of Ignoring API Security
In 2023, a leading global fintech platform suffered a $4 million data breach because of an untested API endpoint. The flaw?
A forgotten debugging endpoint allowed unauthorized users to access customer transaction data through a simple GET request.
After the breach, their VAPT revealed multiple unencrypted endpoints and misconfigured tokens across internal APIs — issues that could have been detected early with regular testing.
This incident reinforced one message for businesses worldwide: Unsecured APIs can quietly become your most significant security liability.
How Infosprint Technologies Secures APIs with VAPT
At Infosprint Technologies, we conduct comprehensive API VAPT assessments combining manual and automated techniques for unmatched accuracy.
Our process includes:
- Deep endpoint analysis using OWASP and NIST frameworks
- Token and authentication testing across OAuth, JWT, and SSO integrations
- Parameter tampering, fuzzing, and injection validation
- Detailed reporting with actionable remediation guidance
- Retesting to verify patch effectiveness
Our goal: To help your organization stay resilient, compliant, and breach-free — while enabling developers to deploy secure APIs faster.
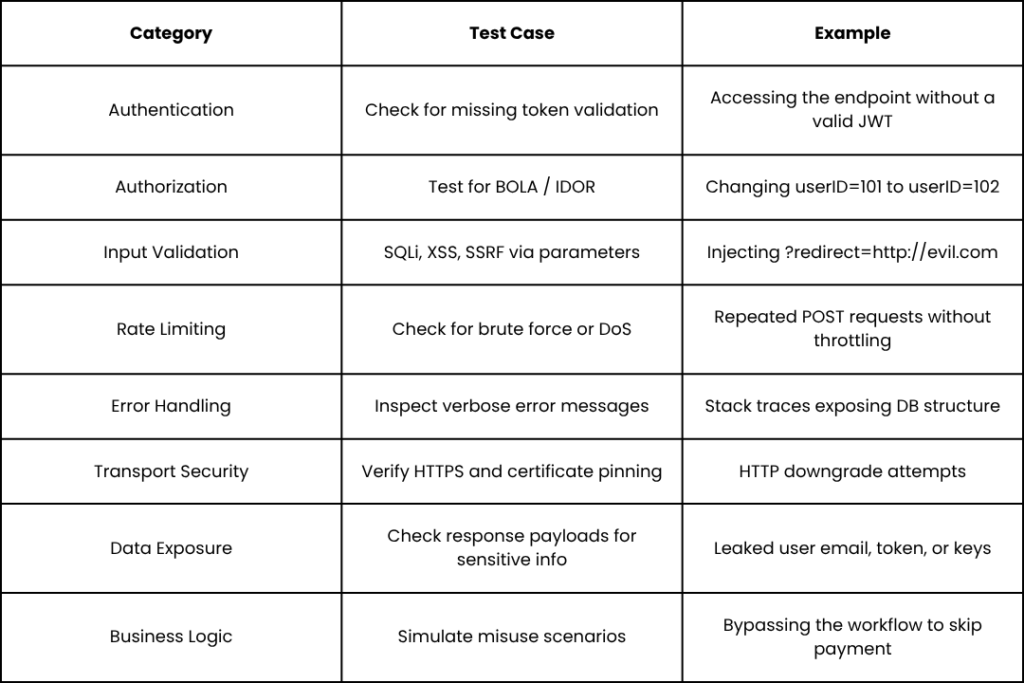
Checklist: API VAPT Test Cases That Catch Real Flaws
Here’s a practical API VAPT checklist — the same one Infosprint’s security engineers use during endpoint testing:
Don’t Let APIs Be Your Weakest Link
APIs are the digital nervous system of modern enterprises — and securing them is no longer optional.
API VAPT ensures your endpoints stay one step ahead of attackers by continuously identifying vulnerabilities, testing real-world exploitability, and strengthening overall resilience.
Whether you manage customer-facing APIs or internal microservices, regular VAPT assessments are your best defense against data leaks, compliance risks, and brand damage.
Let our experts help you identify hidden vulnerabilities before attackers do. Get in Touch with Our Security Team
Frequently Asked Questions
API VAPT identifies vulnerabilities in APIs through testing, helping prevent data leaks and unauthorized access before attackers exploit them.
At least once a year or after major updates—more frequently for high-risk or customer-facing APIs.
Broken authentication, data exposure, weak rate limiting, and injection flaws are the most common security gaps.
Yes. Regular API VAPT supports compliance with GDPR, PCI-DSS, HIPAA, and ISO 27001 by proving proactive risk management.
Primarily in staging to avoid service disruption, but limited safe testing can also be done in production environments.
Proactive testing can save up to 10x in potential breach costs by preventing data loss, regulatory fines, and customer churn.
Related Blogs
Top 10 Cloud Computing Technologies to Look Out for in 2025

Consistent Diagnosis: The Cornerstone of Modern Healthcare




