5 Ways Social Engineering Gets More Sophisticated During Holiday Sales — and How to Defend
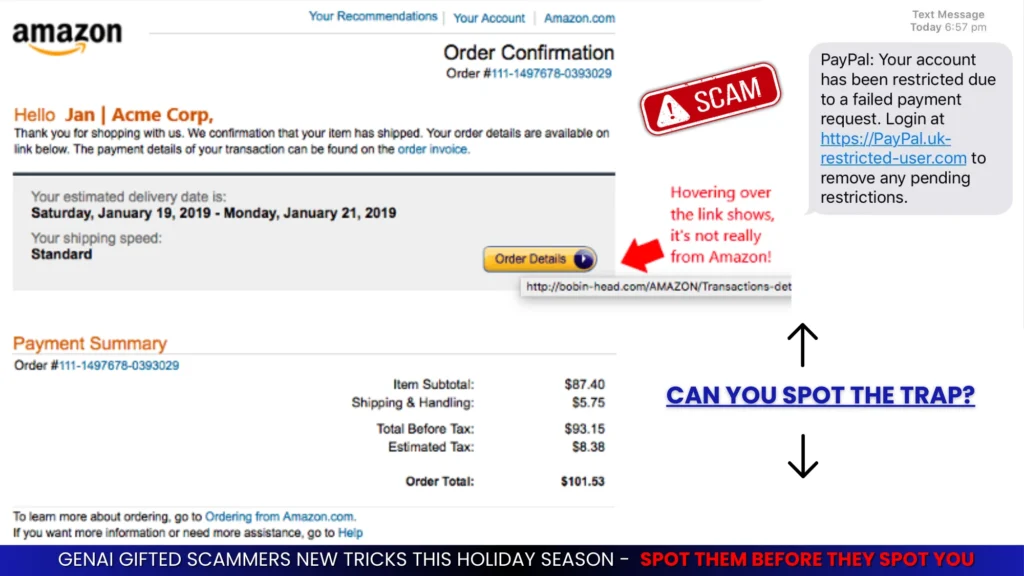
Cybercriminals don’t take holidays — they wait for yours.
In 2024, holiday phishing attempts increased by over 80%, resulting in millions of dollars in losses.
Every holiday season, the inbox overflows with shipping updates, flash sales, and “exclusive” deals. Behind that excitement, attackers see the perfect storm: massive order volumes, distracted shoppers, and understaffed IT teams. Each alert or coupon becomes a potential gateway for fraud.
With emotions high — urgency, generosity, and trust — social engineers strike hardest. Fake order confirmations, cloned brand stores, and voice scams disguised as “delivery support” prey on people when their guard is down.
At Infosprint Technologies, we help businesses stay a step ahead of these evolving cyberattacks. This guide unpacks five advanced social engineering tactics increasing during festive sales — and how your organization can defend against them using more innovative GRC strategies, AI-powered filters, and real-world awareness.
The 5 Ways (and how to defend each)
The festive season excitement is real — but also serves as a gateway for hackers. Here are five evolving social engineering tactics thriving amid holiday sales chaos, and how your team can defend against them before they strike.
1)Hyper-personalization at scale (GenAI-driven spear phishing)
What it looks like:
Attackers use Large Language Models and public data (social posts, purchase history, scraped profiles) to generate individualized emails/messages that reference recent purchases, local events, or colleagues’ names. These messages sound natural — sometimes indistinguishable from real emails.
Why this matters in holiday sales:
Shoppers expect receipts, delivery updates, and targeted offers. A personalized “Your Diwali order from X failed — update payment” email will get more clicks.
Attackers no longer send generic links; instead, they mirror your digital footprint.
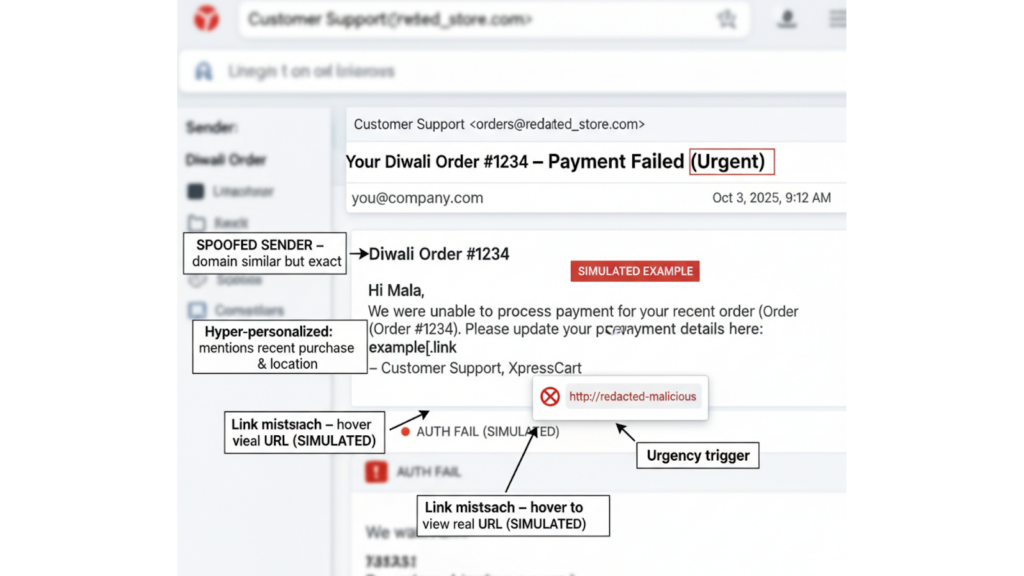
When festive inbox noise peaks, even the most vigilant users can miss these subtle red flags. Training teams to slow down and hover before they click can prevent a costly breach.
Defenses — practical steps
- Email authentication: Enforce SPF, DKIM, and DMARC with a reject/quarantine policy.
- Contextual link checks: Deploy URL-inspection tools that compare link domains against genuine merchant domains and flag suspicious redirects.
- Behavioral detection: Utilize machine-learning anti-phishing techniques that score messages based on personalization signals and origin anomalies.
- User training: Show employees and customer support examples of hyper-personalized phishing (your audio/video inserts here). Teach the “slow hover” rule: hover links, then open the real site manually.
- Prompt-style content you can embed: “Show example: ‘Your order #1234 — payment failed’ email (realistic phishing sample generated by LLM).”
2)Cross-channel orchestration: email → WhatsApp → voice (coordinated attacks)
What it looks like:
Attackers initiate contact via email, follow up on WhatsApp with a “support agent,” and make calls using spoofed caller IDs. The multi-channel approach builds trust through repetition and apparent verification.
Why this matters:
Consumers often assume consistency across channels equals legitimacy. A message that appears in both WhatsApp and via a phone call seems to be “verified.”
Defenses — practical steps
- Channel verification policies: For any claim involving money or credentials, verification is required on an official app or website — not via a forwarded WhatsApp link or an unknown phone number.
- Business account best practices (WhatsApp): Encourage customers to confirm the green/verified badge and list exact business handles on your website.
- Call-back policy: Clearly state (on your website and in emails) that you will never request OTPs or full card details over calls or chats; instruct customers to hang up and call your official number instead.
- Monitoring: Track mentions of your brand across channels to quickly identify phishing clones and fake business accounts.
Social engineering attacks surged in the first half of 2025 – LevelBlue report
3)Business-logic abuse & API-level attacks (bots & automated fraud)
What it looks like:
Instead of tricking a user, attackers exploit pricing logic, discount code systems, or payment APIs to siphon value: automated bots, replayed API calls, or manipulated discount stacking.
Why this matters:
Holiday promotions increase the number of promo codes, loyalty flows, and API calls — magnifying the consequences of a logic flaw.
Defenses — practical steps
- API hardening: Enforce strong authentication (OAuth2, mTLS where feasible), strict rate limiting, and anomaly detection for unusual volumes or patterns.
- Business logic testing: Include business logic VAPT in pre-holiday checklists — test promo stacking, price manipulation, and refund flows.
- Bot mitigation: Utilize device and behavior fingerprinting, CAPTCHA for high-risk flows, and automated bot-traffic detection.
- Monitoring & rollback: Monitor refund/chargeback rates closely and be ready to revoke suspicious promo codes or pause risky campaigns.
4)Voice cloning & deepfake vishing
What it looks like:
Attackers use voice-cloning tools to impersonate executives or customer-service representatives, or generate realistic voicemail prompts to trick users into calling back a scam line.
Why this matters:
Voice is trusted. When holiday shoppers get a call “from the bank” with a cloned familiar voice, it’s persuasive — and OTPs or confirmation codes may be shared.
Defenses — practical steps
- Always call back protocols: Train staff & customers to hang up and call the verified number on the bank/merchant site.
- Multi-factor verification for sensitive actions: Never rely on a single OTP delivered via SMS/call for high-risk account changes. Use app-based 2FA and secondary confirmation channels.
- Deepfake detection & vendor solutions: For enterprise hotlines, consider voice-biometric checks or services that detect synthetic audio patterns (where applicable).
- Employee awareness drills: Run vishing simulations and record performance metrics to close awareness gaps.
Attackers can use generative AI to imitate familiar voices, such as those of your CEO or manager. A single urgent call could lead to immediate, irreversible actions.
“Hearing your boss’s voice is more convincing than reading their email. That’s what makes voice phishing—also known as vishing—so dangerous.”
5)Third-party & supply-chain social engineering
What it looks like:
Attackers compromise delivery vendors, payment processors, or third-party widgets, and use that access to send trusted messages (such as shipping delays or invoice requests) or embed malicious scripts in checkout pages.
More than one-third of social engineering incidents involved non-phishing techniques
Why this matters:
During festive seasons, companies rely more on third-party tools for logistics, invoicing, and promotions. A compromise in one vendor can cascade.
Defenses — practical steps
- Third-party risk assessments: Maintain an updated inventory of suppliers, run periodic security questionnaires, and require vendors handling customer data to implement minimum security controls.
- Content integrity checks: Monitor third-party script changes and set alerts for unexpected hostnames or resource calls from payment pages.
- Secure onboarding & revocation: Have rapid revocation plans and alternate vendors in case of a vendor compromise.
- Contractual SLAs & security clauses: Ensure vendors are contractually obligated to report incidents and perform penetration tests.
For businesses running large festive campaigns, securing every customer touchpoint is vital. Implement layered defenses through cybersecurity solutions that combine phishing protection, access control, and endpoint monitoring to reduce risk during high-traffic periods.
Countermeasures — a layered defence approach
- People: Regular, scenario-based training, phishing simulations, and holiday-season readiness drills.
- Process: Clear verification policies (call-back, payment confirmation), minimal change windows during peak hours, and incident escalation flow with defined SLAs.
- Technology: Email auth (SPF/DKIM/DMARC), EDR/XDR, phishing filters, behavioral anomaly detection, API security gateways, WAF, bot management, and voice deepfake detection tools where relevant.
- GRC & Testing: Run targeted VAPT (business-logic & API tests) before promotions go live and update GRC documentation with festive-season playbooks.
The Festive Season Is About Joy — Don’t Let It Turn Into a Cyberstorm
Social engineering works because it exploits trust — not technology. As GenAI deepens the realism of fake communication, even cautious users can be deceived. Businesses that combine GRC awareness, VAPT testing, and AI-based protection are far more resilient against these evolving threats.
LLMs are guessing login URLs, and it’s a cybersecurity time bomb. – CSO
At Infosprint Technologies, we help organizations build human firewalls — teams that recognize deception before it causes damage. Our experts conduct realistic phishing simulations and strengthen compliance frameworks to ensure you stay safe, even during high-risk festive periods.
👉 Need a phishing simulation tailored for your team?
Schedule a free GRC consultation today and get your festive security readiness assessed.
Frequently Asked Questions
Check for a verified badge, confirm their exact business handle on the brand’s website, never share OTPs, and avoid clicking shortened links.
Not necessarily — voice cloning exists. Always call back using the official number.
Disconnect, change passwords (starting with email), notify your bank/IT team, and run a device scan.
Yes. GenAI makes personalized, context-aware phishing easier. Layered defense and user awareness are critical.
Schedule final security testing before live promotions and prepare rapid rollback plans instead of pausing mid-campaign.
Related Posts
Top 10 Cloud Computing Technologies to Look Out for in 2025

Consistent Diagnosis: The Cornerstone of Modern Healthcare




